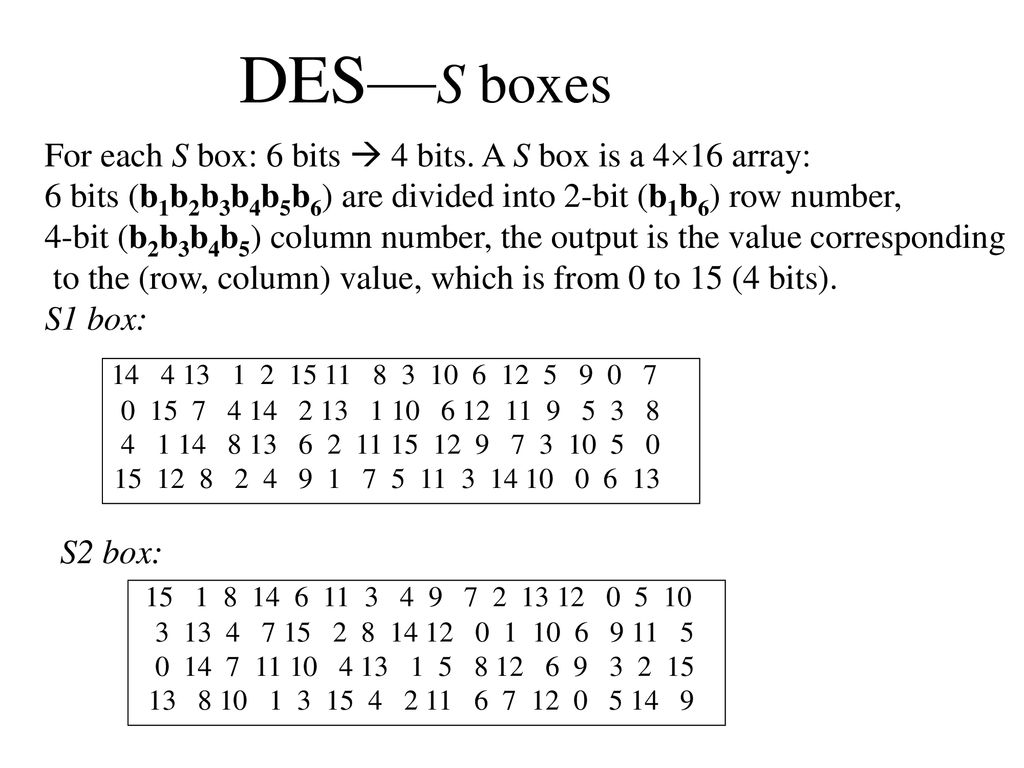
S Boxes In Des
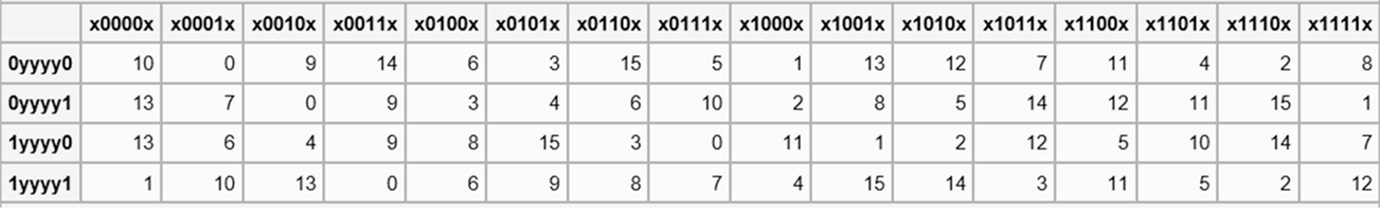
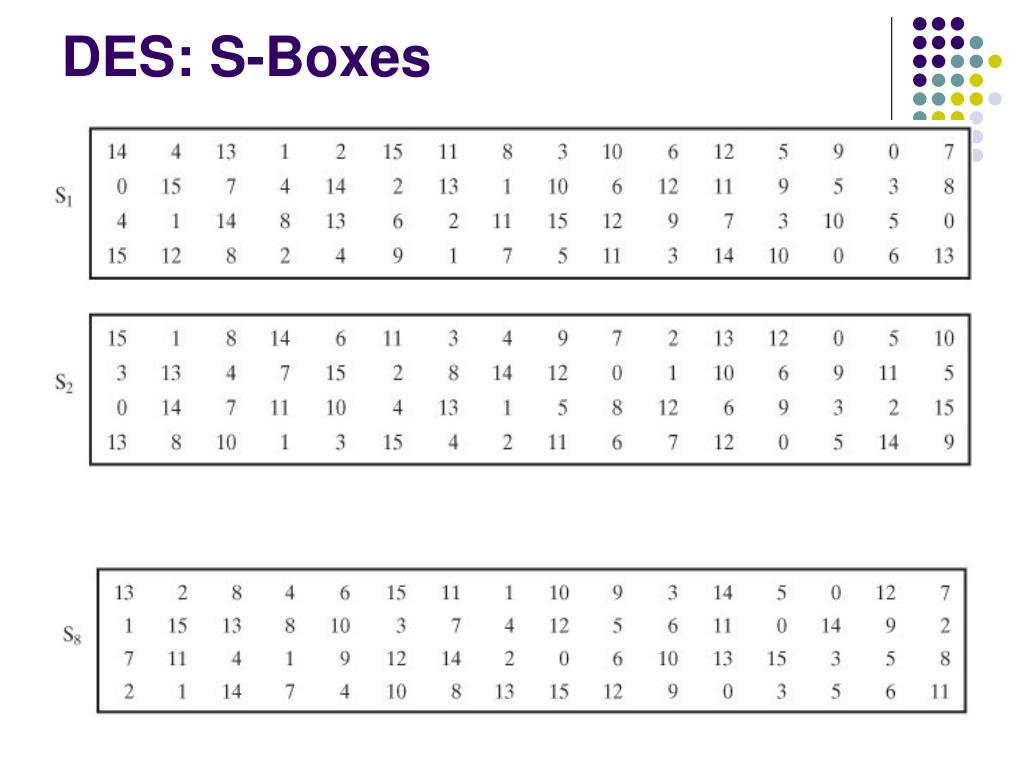
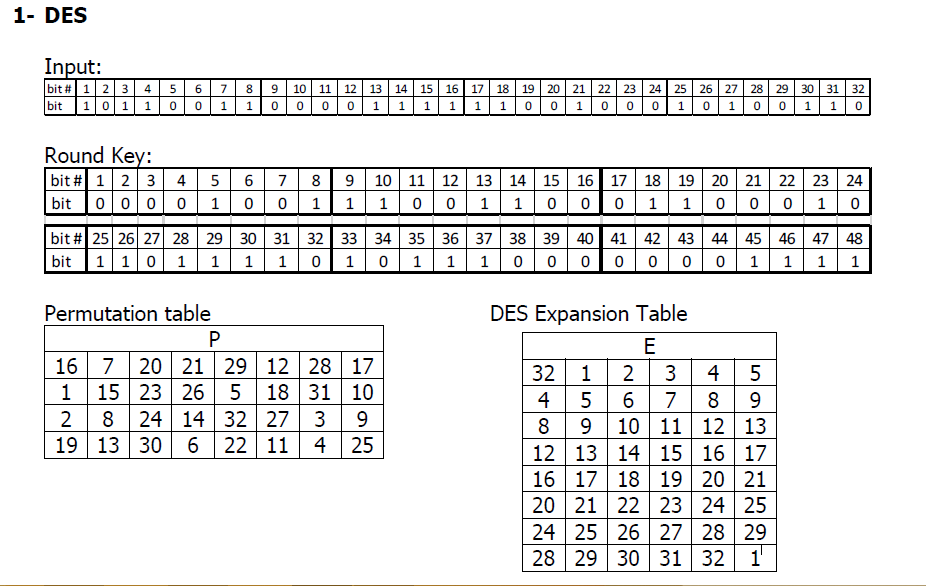
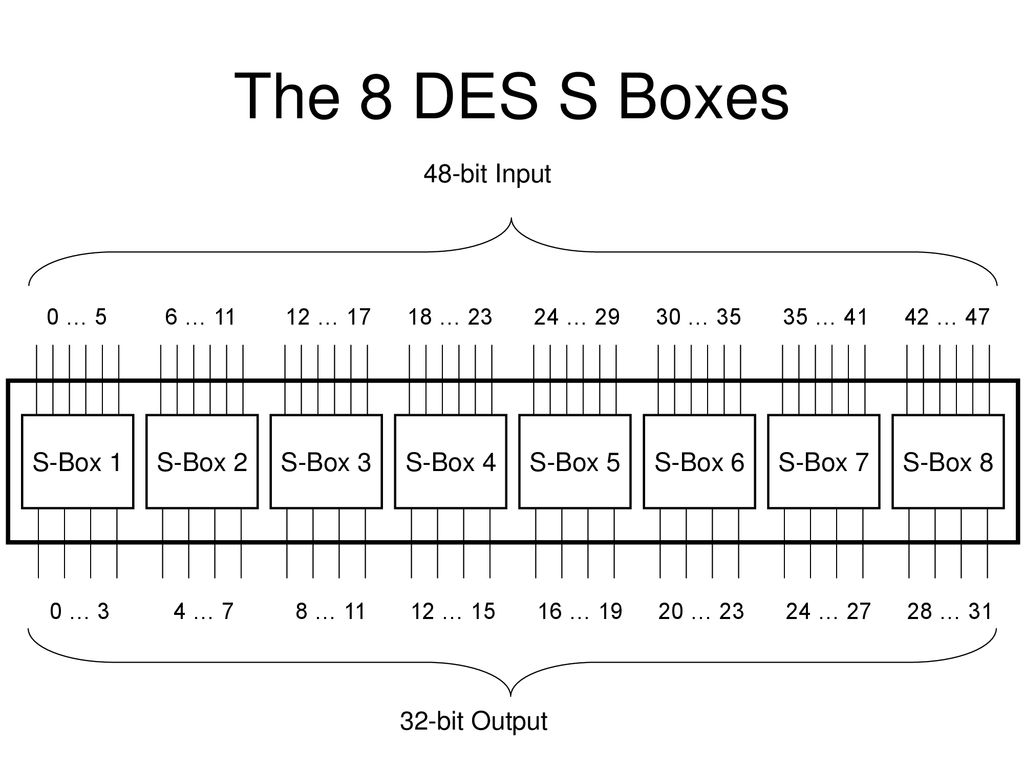
Sboxes • Sboxes are the only nonlinear elements in DES design • S = matrix 4x16, values from 0 to 15 • B (6 bit long) = b1b2b3b4b5b6 – b1b6 r = row of the matrix (2 bits 0,1,2,3) – b2b3b4b5 c = column of the matrix (4 bits0,1,15) • C (4 bit long) = Binary representation of S(r, c) B (6 bit) C (4 bit)SBox 8 SBox 17.
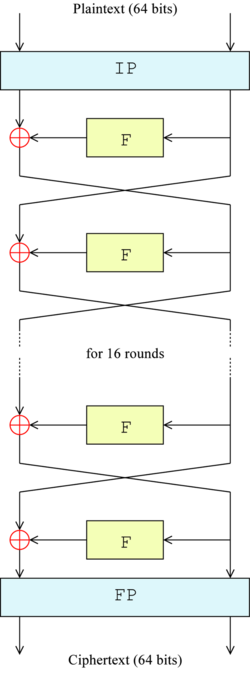
S boxes in des. Storage (in bytes) = Number of Sboxes x 2 Number of input bits x (Number of output bits / 8) So DES = 8 x 2 6 x (4 / 8) = 256 bytes AES = 1 x 2 8 x (8 / 8) = 256 bytes. DES Numerology • DES is a Feistel cipher • 64 bit block length • 56 bit key length • 16 rounds • 48 bits of key used each round (subkey) • Each round is simple (for a block cipher) • Security depends primarily on “Sboxes” • Each Sboxes maps 6 bits to 4 bits Initial Permutations • DES has an initial permutation and a final. Furthermore, how would one reverse uneven SBoxes, such as DES's 6x4 SBox, when multiple inputs give the same output (eg, for DES's SBox S 5, where inputs of , , , and all give an output of 1000).
Diethylstilbestrol (DES) is an estrogen that was first manufactured in a laboratory in 1938, so it is called a "synthetic estrogen" During , US physicians prescribed DES to pregnant women to prevent miscarriages and avoid other pregnancy problems. DES specifications •64bit block cipher •56bit key (the key is technically 64 bits but 8 are used as parity bits for error correcting making the effective security equivalent to a 56bit key) •16 round Feistel cipher •The round function requires 48 bits of input –Uses 8 Sboxes of 6bits each •Different 48 subkey used for each round. Diethylstilbestrol (DES) is an estrogen that was first manufactured in a laboratory in 1938, so it is called a "synthetic estrogen" During , US physicians prescribed DES to pregnant women to prevent miscarriages and avoid other pregnancy problems.
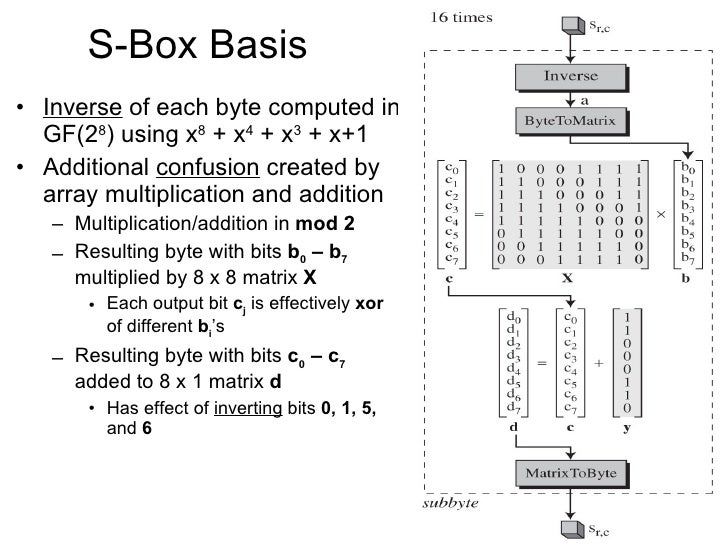
Compared to AES, the structure of DES uses fewer types of primitive operations – only bitbybit permutations/ expansions, XOR, and eight 6bitto4bit Sboxes – whereas AES uses byte shifting, XOR, one 8bitto8bit Sbox, and field multiplication. How DES works Encryption of a block of the message takes place in 16 stages or rounds From the input key, sixteen 48 bit keys are generated, one for each round In each round, eight socalled Sboxes are used These Sboxes are fixed in the specification of the standard Using the Sboxes, groups of six bits are mapped to groups of four bits. In cryptography, a SBox (Substitutionbox) is a basic component of symmetrickey algorithms In block ciphers, the SBoxes are used to make the relation between the key and the ciphertext (coded text) difficult to understand– Shannon's property of confusion The SBoxes are carefully chosen to resist cryptanalysis (decoding).
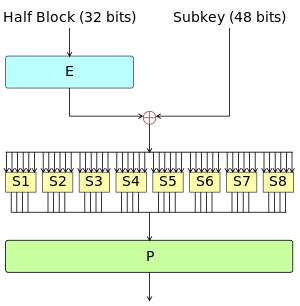
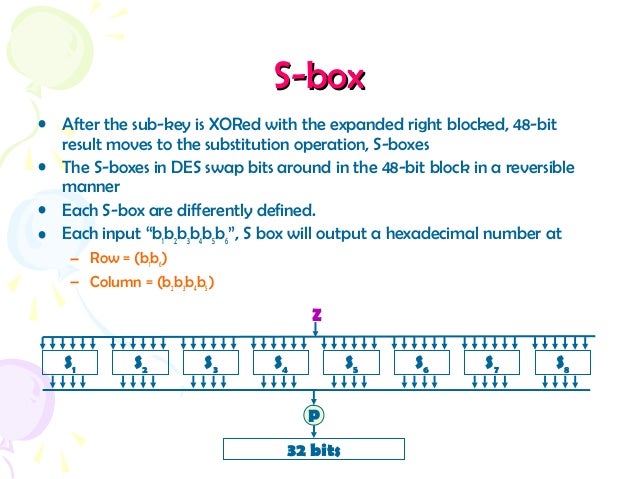
Sboxes in DES are nonlinear show that S1(X1) XOR S1(X2) is not S1(x1 XOR x2) x1= x2=. Compared to AES, the structure of DES uses fewer types of primitive operations – only bitbybit permutations/ expansions, XOR, and eight 6bitto4bit Sboxes – whereas AES uses byte shifting, XOR, one 8bitto8bit Sbox, and field multiplication Because of the heavy use of bit permutations, I chose to implement the DES spreadsheet by giving each bit its own cell, instead of constantly assembling and disassembling multibit integers (whereas in AES I always handled whole bytes). Data Encryption Standard (DES) 147 DES Function K I (48 bits) f ( R I–1, K I 48 bits) Out S S S S S S S S Straight Dbox Expansion Dbox SBoxes XOR 32 bits In 48 bits 32 bits 32 bits Fig 65 DES function The heart of DES is the DES function The DES function applies a 48bit key to the rightmost 32 bits (R I−1) to produce a 32bit output This function is.
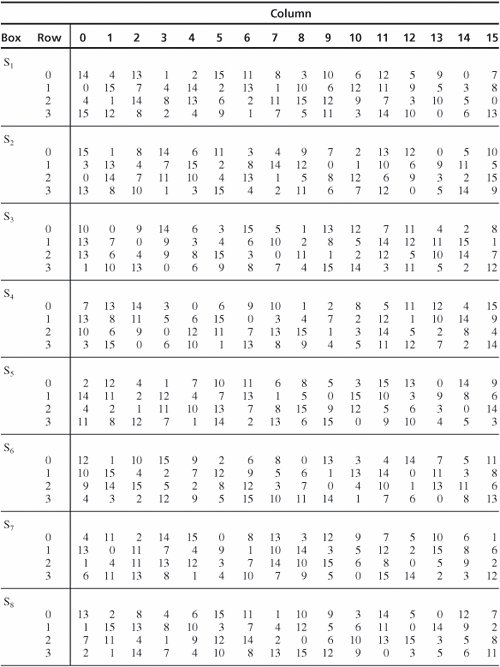
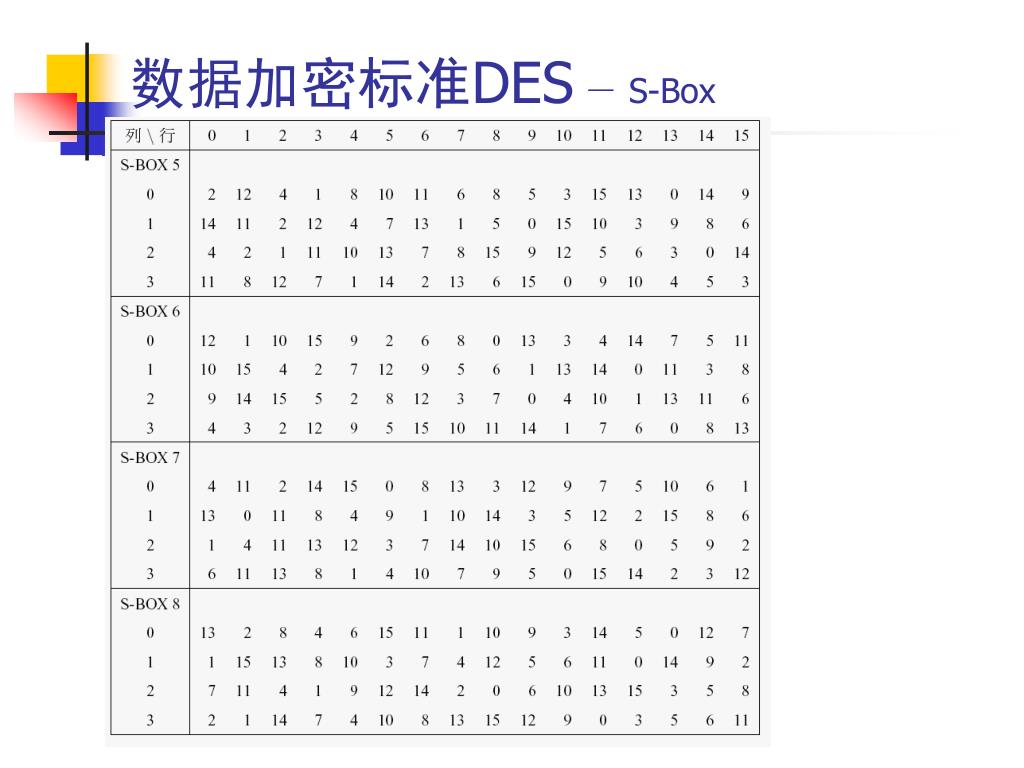
DES uses eight separate tables or Sboxes, a different one for each 6 bits of data The following table shows the eight Sboxes of DES The eight separate Sboxes are used to translate each 6bit input into a 4bit output. (in Decimal) What Is S1(212)?. Sboxes • Sboxes are the only nonlinear elements in DES design • S = matrix 4x16, values from 0 to 15 • B (6 bit long) = b1b2b3b4b5b6 – b1b6 r = row of the matrix (2 bits 0,1,2,3) – b2b3b4b5 c = column of the matrix (4 bits0,1,15) • C (4 bit long) = Binary representation of S(r, c) B (6 bit) C (4 bit)SBox 8 SBox 17.
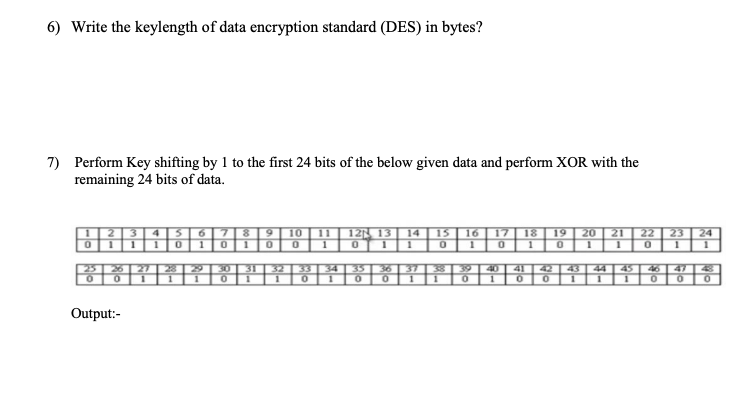
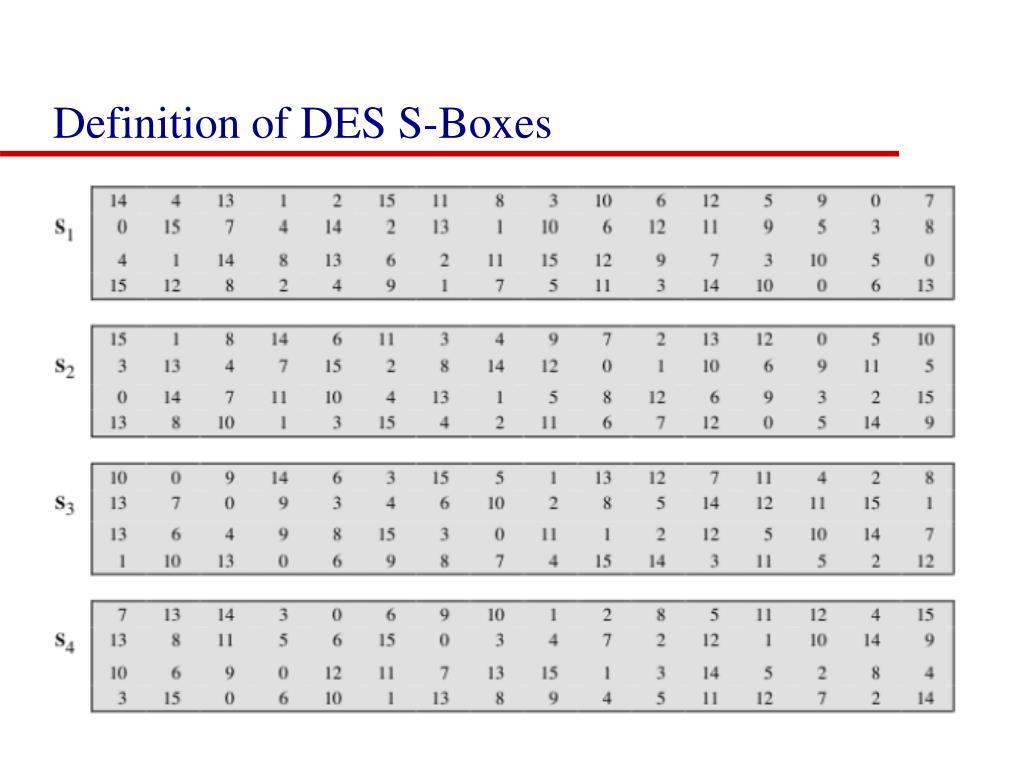
The Sboxes are the nonlinear part of DES that makes it difficult to break the algorithm and secure against linear and differential cryptanalysis the sboxes provide the "confusion" of data and. DES specifications •64bit block cipher •56bit key (the key is technically 64 bits but 8 are used as parity bits for error correcting making the effective security equivalent to a 56bit key) •16 round Feistel cipher •The round function requires 48 bits of input –Uses 8 Sboxes of 6bits each •Different 48 subkey used for each round. DES uses eight separate tables or Sboxes, a different one for each 6 bits of data The following table shows the eight Sboxes of DES The eight separate Sboxes are used to translate each 6bit input into a 4bit output.
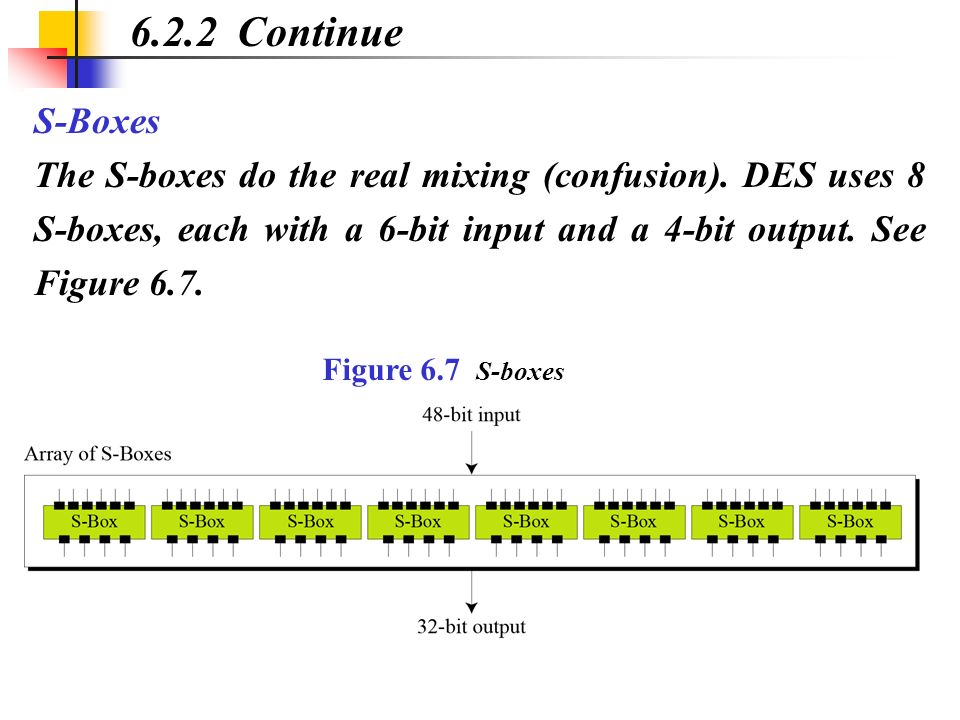
SBoxes The Sboxes do the real mixing (confusion) DES uses 8 Sboxes, each with a 6bit input and DES uses 8 Sboxes, each with a 6bit input and a 4bit output. The Sboxes are the nonlinear part of DES that makes it difficult to break the algorithm and secure against linear and differential cryptanalysis the sboxes provide the "confusion" of data and. Phic algori thms use DES like s boxes, and are implemented boxes can be analyzed in detail, a general look at the DES ANSI X392 algorithm is needed There are many block ciphers to choose from that boxes);.
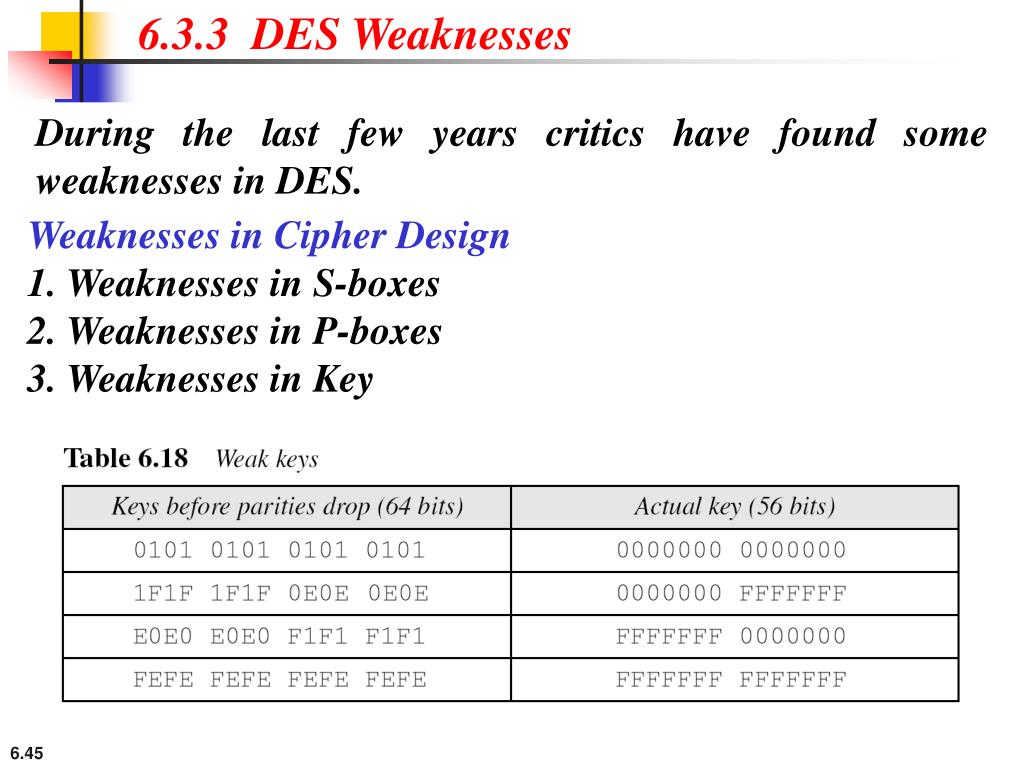
Note that Rijndael still uses an Sbox with 256 entries, each eight bits long, which is much larger than the Sboxes with 64 entries, each four bits long, used in DES The larger an Sbox is, the easier it is to prepare one with a useful degree of resistance to linear and differential cryptanalysis. SDES or Simplified Data Encryption Standard The process of encrypting a plan text into an encrypted message with the use of SDES has been divided into multisteps which may help you to understand it as easily as possible Points should be remembered It is a block cipher. The complete specifications of the Sboxes have remained secret This has lead some to believe that NSA has a backdoor into the DES algorithm To allay these suspicions in the early 1990's IBM published its design criteria for the Sboxes These indicated that the Sboxes were designed to thwart certain sophisticated attacks (especially differential.
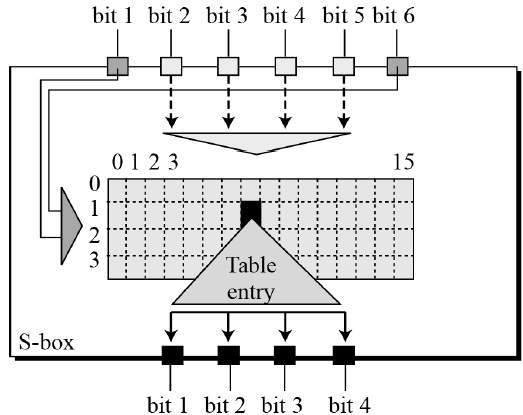
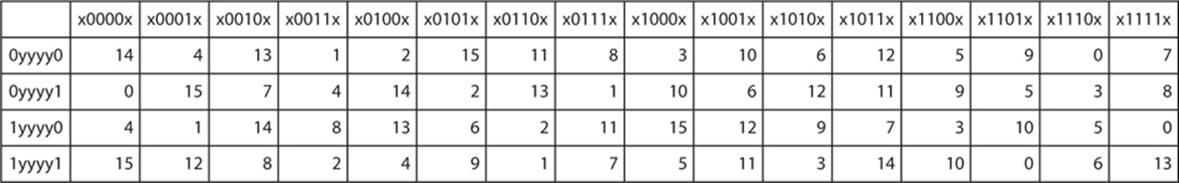
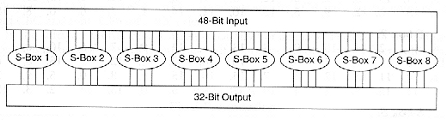
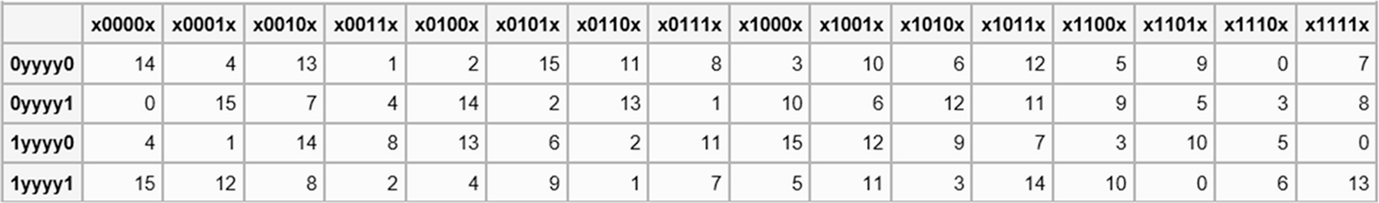
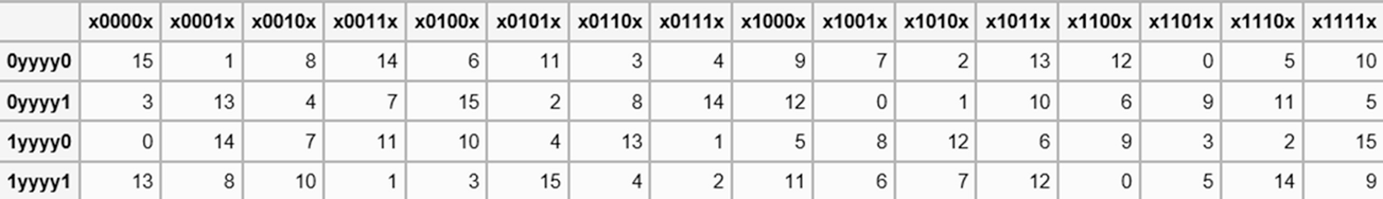
The eight Sboxes of DES were the subject of intense study for many years out of a concern that a backdoor (a vulnerability known only to its designers) might have been planted in the cipher The Sbox design criteria were eventually published (in Coppersmith 1994 ) after the public rediscovery of differential cryptanalysis , showing that they had been carefully tuned to increase resistance against this specific attack. Each table contains 4 rows and 15 columns, where bits ( x1, x2, x3, x4) identify a column in the table. Substitution boxes S box In DES algorithm we have 8 S boxes Input for S box is 48bit And output from S box is 32 bit The input 48 bit will be divided equally to 8 s boxes from s1, s2, s8 So each s box will get 48/8= 6 bits as input This Each S box reduce 6 bits to 4 bits ie input for each S box is 6 bits and output is 4 bits.
In this walkthrough, we've shared how to link text boxes in InDesign, so that your article continues from one column (or page) to the next InDesign link text boxes is essential when designing magazine and newspaper layouts, since you need text to flow seamlessly across multiple pages. Sequential application of confusion and diffusion Typically, confusion is provided by some form of substitution ("Sboxes") So the obvious question is whether some substitutions are better than others The obvious answer is "Yes," because one possible substitution maps every value onto itself, just as though there. In cryptography, the avalanche effect is a term associated with a specific behavior of mathematical functions used for encryptionAvalanche effect is considered as one of the desirable property of any encryption algorithm A slight change in either the key or the plaintext should result in a significant change in the ciphertext.
Substitution Boxes − The Sboxes carry out the real mixing (confusion) DES uses 8 Sboxes, each with a 6bit input and a 4bit output Refer the following illustration −. 93 THE DES SBOXES, PBOX, AND INITIAL PERMUTATION (IP) Tables 94 to 911 specify the seven DES Sboxes, each with a 6bit input ( x0, x1, x2, x3, x4, x5, x6) and a 4bit output ( y0, y1, y2, y3 );. Question (1 Point) This Question Concerns The DES Sboxes Please Enter All Answers In Decimal Consider The Two 6bit Numbers X1 And 22 What Is $1(3)?.
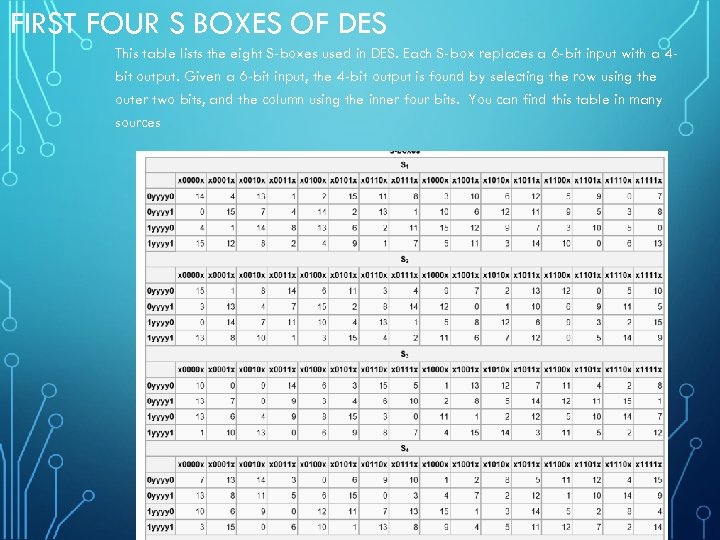
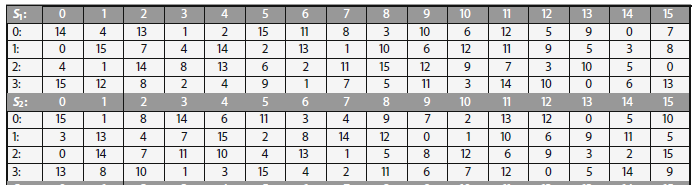
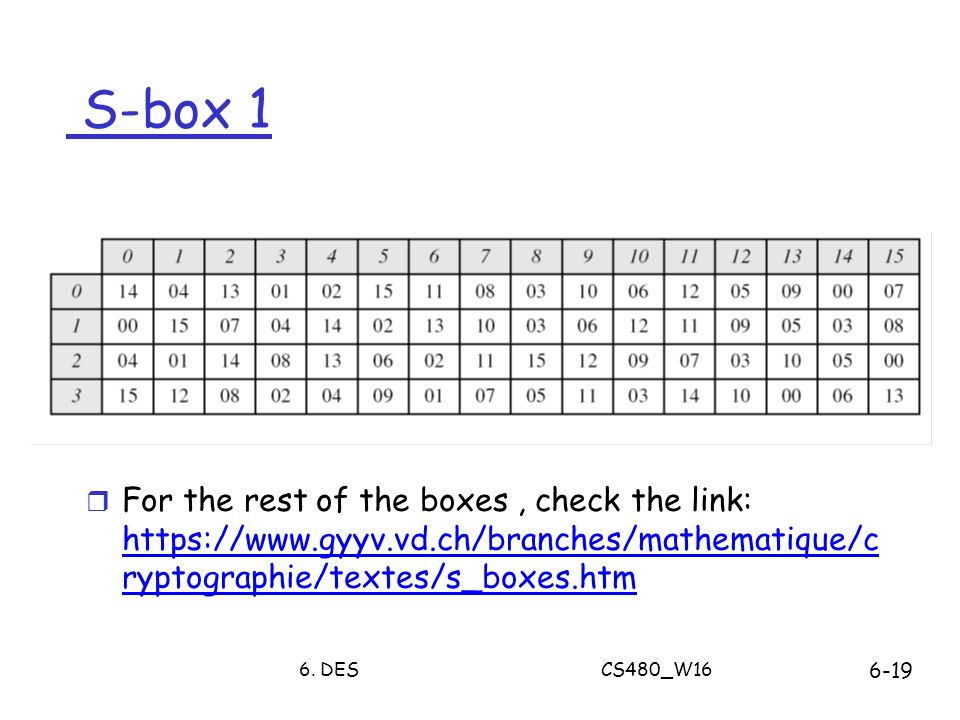
It turns out that although the DES designers did not know of linear cryptanalysis (discovered in 1993 by Matsui), having Sboxes which resist differential cryptanalysis kinds of defeats linear cryptanalysis as well. Substitution boxes (Sboxes) This table lists the eight Sboxes used in DES Each Sbox replaces a 6bit input with a 4bit output Given a 6bit input, the 4bit output is found by selecting the row using the outer two bits, and the column using the inner four bits. Instructor We're taking the first big stepinto the structure of modern block ciphersNow we'll talk about Sboxes and PboxesSubstitution boxes and permutation boxesare key components of modern block ciphersSboxes are nonlinear transformationsof a few input bits that provide confusionand Pboxes simply shuffle the input bits aroundto provide diffusion as we've.
DES has 6 x 4 Sboxes Blowfish, described in Chapter 6, has 8 x 32 Sboxes Larger Sboxes, by and large, are more resistant to differential and linear cryptanalysis SCHN96 On the other hand, the larger the dimension n, the (exponentially) larger the lookup table Thus, for practical reasons, a limit of n equal to about 8 to 10 is usually imposed Another practical consideration is that the larger the Sbox, the more difficult it is to design it properly. 1/2 Price Boxes W Houston 5475 West Loop South Next door to Boudreaux's Suite 1 Houston, TX Phone 1/2 Price Boxes Sugar Land 1st Colony Commons Shopping Ctr. Sbox In cryptography, an SBox (Substitutionbox) is a basic component of symmetric key algorithms which performs substitution In block ciphers, they are typically used to obscure the relationship between the key and the ciphertext — Shannon's property of confusion In many cases, the SBoxes are carefully chosen to resist cryptanalysis.
" the inverses of the DES 4x4 Sboxes meet the acknowledged DES design criterion which requires that at least two bits change in the output whenever one input bit is changed These two discoveries indicate that the designers of DES placed an equal emphasis on the properties of the Sboxes and their inverses. In cryptography, a SBox (Substitutionbox) is a basic component of symmetrickey algorithms In block ciphers, the SBoxes are used to make the relation between the key and the ciphertext (coded text) difficult to understand– Shannon's property of confusion The SBoxes are carefully chosen to resist cryptanalysis (decoding). Shop from a wide selection of boxes to suit your shipping, moving and packaging needs.
(in Decimaly What Is S1(1102)(in Decimal) What Is Si(2) S1(22)?. The complete specifications of the Sboxes have remained secret This has lead some to believe that NSA has a backdoor into the DES algorithm To allay these suspicions in the early 1990's IBM published its design criteria for the Sboxes These indicated that the Sboxes were designed to thwart certain sophisticated attacks (especially differential. In the field of cryptography, the substitution box (Sbox) becomes the most widely used ciphers The process of creating new and powerful Sboxes never end Various methods are proposed to make the.
The eight Sboxes of DES were the subject of intense study for many years out of a concern that a backdoor (a vulnerability known only to its designers) might have been planted in the cipher The Sbox design criteria were eventually published (in Coppersmith 1994 ) after the public rediscovery of differential cryptanalysis , showing that they had been carefully tuned to increase resistance against this specific attack. However, DES is one of the most widely used and researched encryption algori thms, m aking it valuabl e to study. Phic algori thms use DES like s boxes, and are implemented boxes can be analyzed in detail, a general look at the DES ANSI X392 algorithm is needed There are many block ciphers to choose from that boxes);.
Find moving boxes at Lowe's today Shop moving boxes and a variety of storage & organization products online at Lowescom. Substitution Boxes − The Sboxes carry out the real mixing (confusion) DES uses 8 Sboxes, each with a 6bit input and a 4bit output Refer the following illustration − The Sbox rule is illustrated below − There are a total of eight Sbox tables The output of all eight sboxes is then combined in to 32 bit section. However, DES is one of the most widely used and researched encryption algori thms, m aking it valuabl e to study.
For 4 4 bijective SBoxes the optimal differential bound (maximum of all differentials in an individual SBox) is p= 1=4 Definition 2 Let Sbe an SBox with jSjinput values Let nbe the number of elements xthat satisfy wt( i x o S(x)) mod 2 = 1 for two bitmask vectors i and o. In cryptography, an SBox (Substitutionbox) is a basic component of symmetric key algorithms which performs substitution In block ciphers, they are typically used to obscure the relationship. The DES (Data Encryption Standard) algorithm is the most widely used encryption algorithm in the world For many years, and among many people, "secret code making" and DES have been synonymous (the 4bit outputs from the S boxes) for 32 bits total Write the previous result, which is 48 bits, in the form.
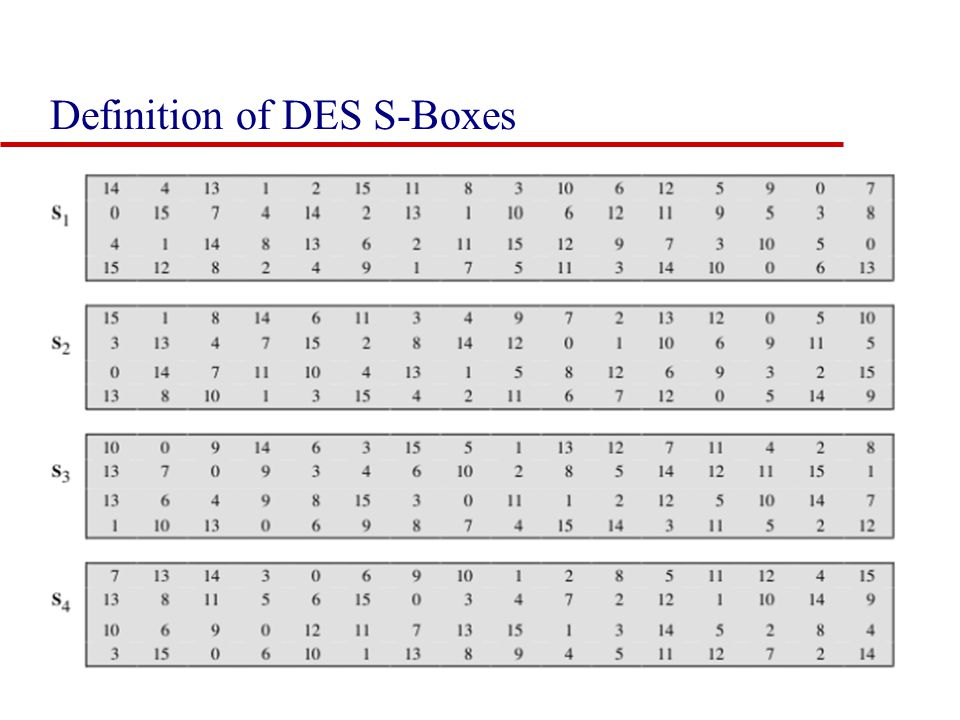
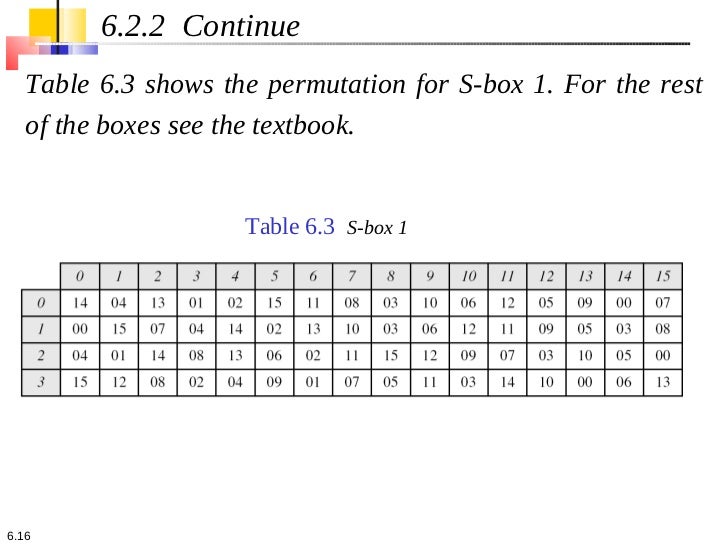
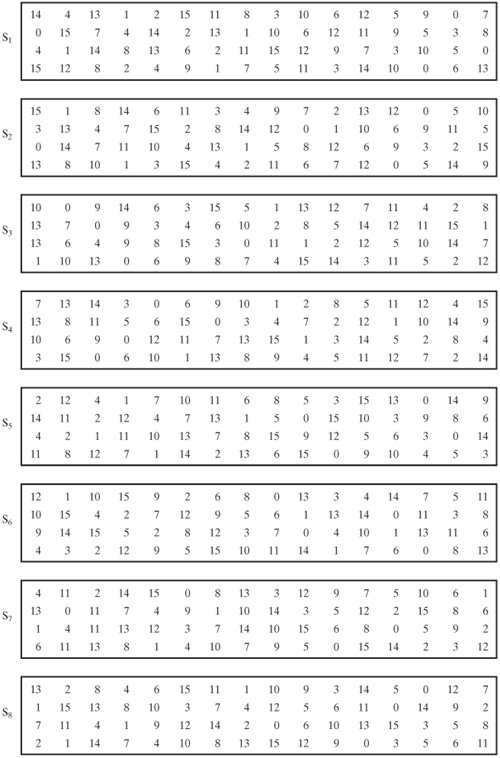
Table 33 Definition of DES SBoxes 14 4 13 1 2 15 11 8 3 10 6 12 5 9 0 7 S1 0 15 7 4 14 2 13 1 10 6 12 11 9 5 3 8 4 1 14 8 13 6 2 11 15 12 9 7 3 10 5 0 15 12 8 2 4 9 1 7 5 11 3 14 10 0 6 13. Hello, I got implementation of Data Encryption Standard implementation in java (internet code) but the only part that I cannot understand is the SBox which shown below I know how SBox works but I don't understand this code especially &0x and stuffs like that The SBox takes a 6 bit word such as as input.
Data Encryption Standard Tutorialspoint

S Box Basic Question Cryptography Stack Exchange

Function S Box S1 In The Des Algorithm Represented As A Table And Its Download Scientific Diagram
S Boxes In Des のギャラリー
Data Encryption Standard Des Set 1 Geeksforgeeks

Function S Box S1 In The Des Algorithm Represented As A Table And Its Download Scientific Diagram

If The First Key Bit Is Flipped Which Des S Boxes Are Affected Cryptography Stack Exchange

Ppt On Des Powerpoint Slides

Pdf Plaintext Recovery In Des Like Cryptosystems Based On S Boxes With Embedded Parity Check Semantic Scholar
Q Tbn And9gcqehpldz7psfjrs7pmbsxxysg 64ocgk26e2p94atioxorqy6m8 Usqp Cau
8 Data Encryption Standard
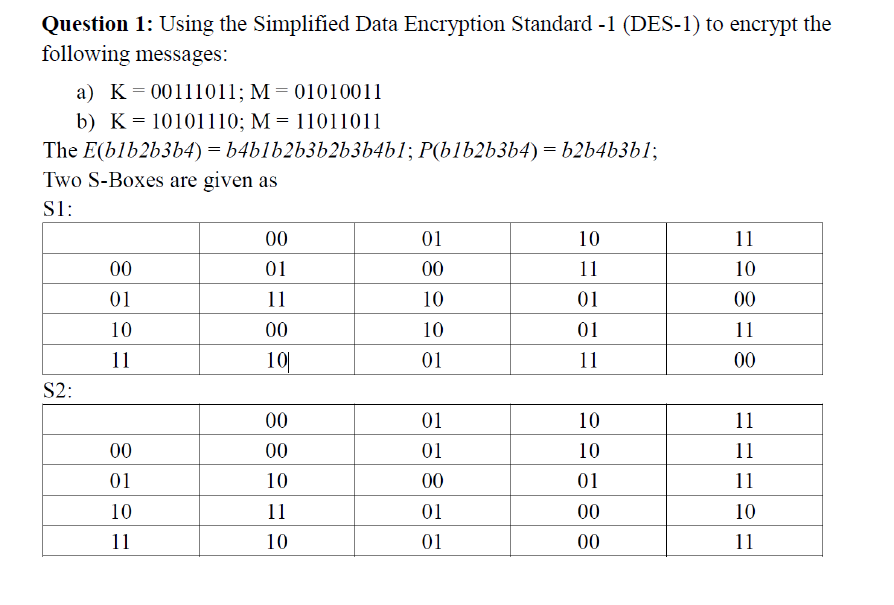
Solved Question 1 Using The Simplified Data Encryption S Chegg Com
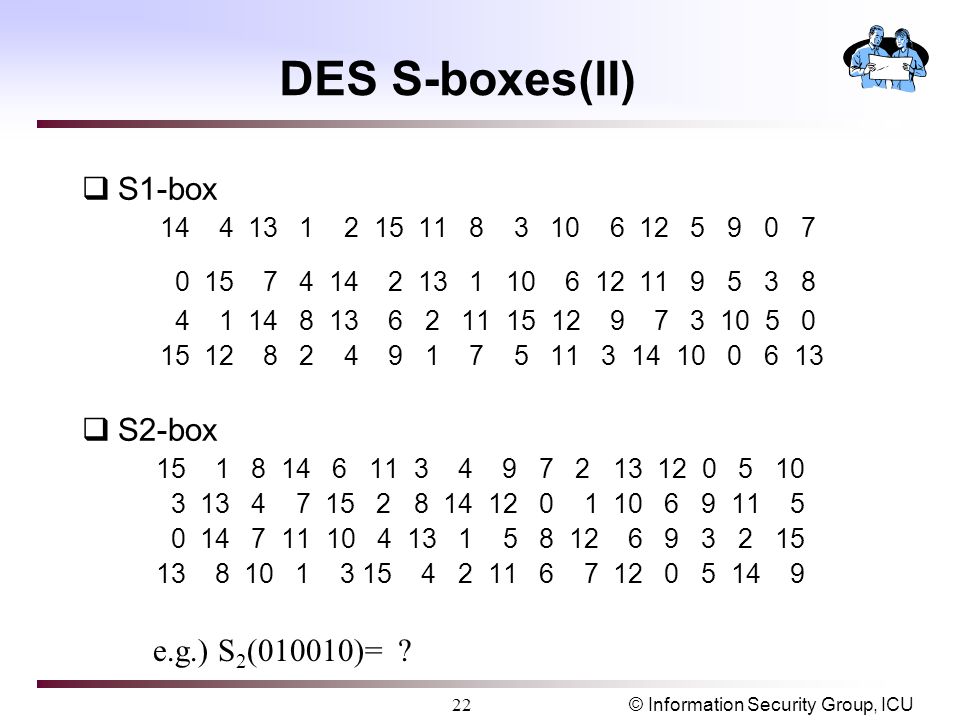
Information Security Group Icu1 Block Cipher Introduction Des Description Feistel S Box Exhaustive Search Dc And Lc Modes Of Operation Aes Description Ppt Download

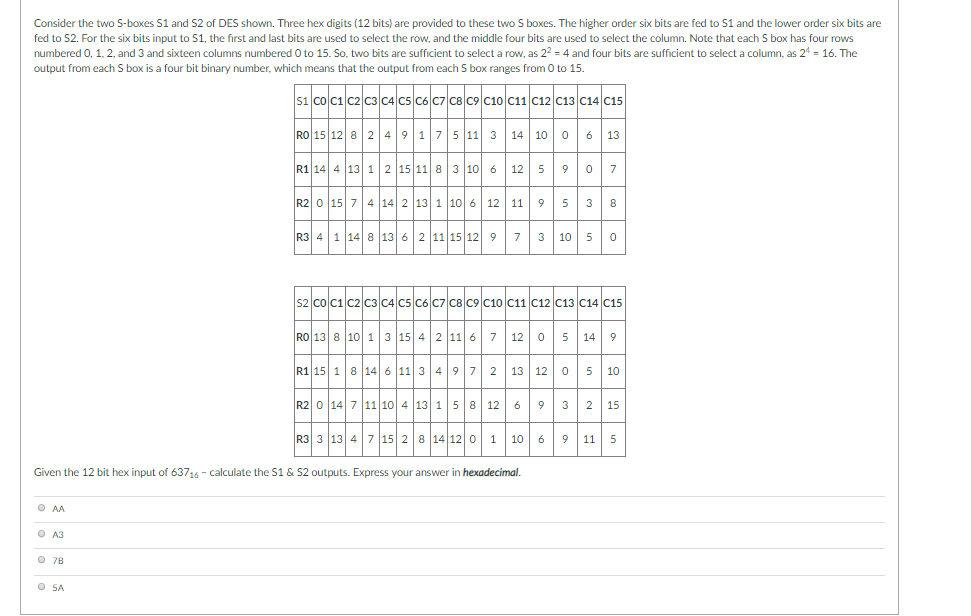
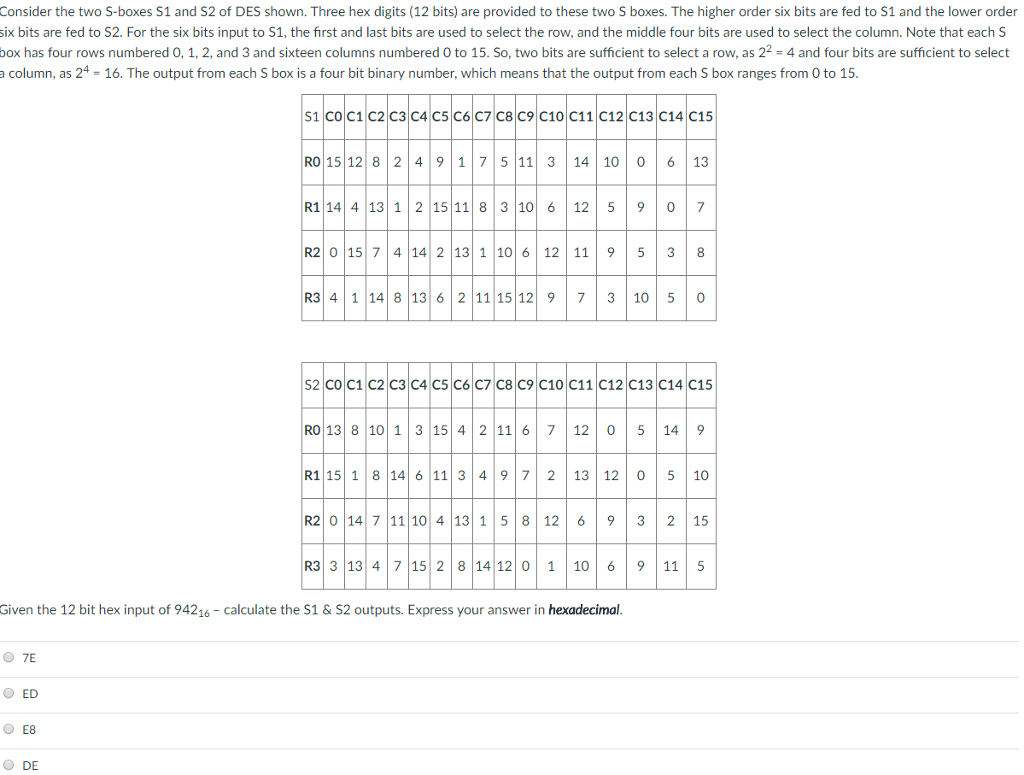
Solved Consider The Two S Boxes S1 And S2 Of Des Shown T Chegg Com

Robustness Of S Boxes Used By Des Download Table

Details Of Des S Boxes Download Scientific Diagram

Ppt On Des Powerpoint Slides

Simplified Des Youtube
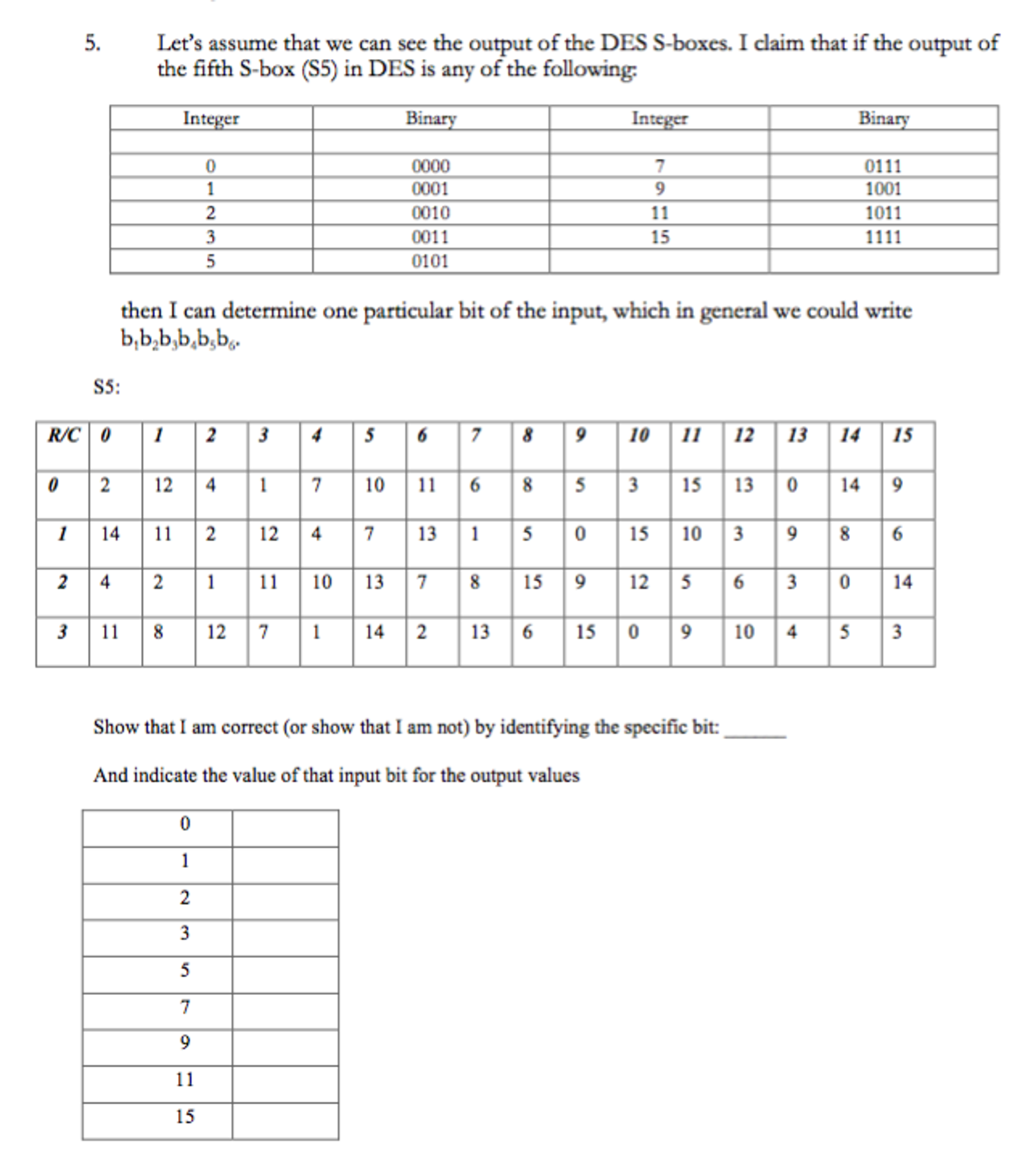
Assume That We Can See The Output Of The Des S Box Chegg Com
Symmetric Cryptography The Basics Symmetric Crytpography Symmetric
S Box Design Springerlink

Table 2 5 From The Block Cipher Companion Semantic Scholar
Section 12 2 Symmetric Encryption Security In Computing 4th Edition

File Des S Box Jpg Wikimedia Commons

Three Symmetric Encryption Algorithm Programmer Sought
Data Encryption Standard Tutorialspoint

Pdf What Do Des S Boxes Say To Each Other Semantic Scholar
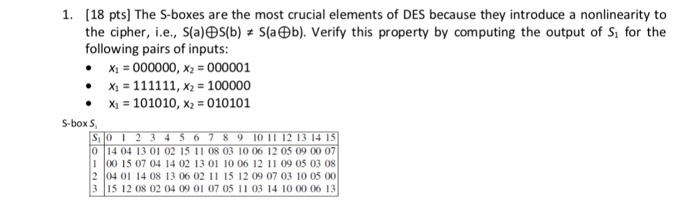
Solved 18 Pts The S Boxes Are The Most Crucial Elements Chegg Com

Data Encryption Standard Tutorialspoint

Marks Find The Result Of The Following Operations A B Course Hero
Q Tbn And9gcsvskl Ol5 Wgf3aikvgc Tqbnnivsvud4qug7wmizavovnhful Usqp Cau

Solved Des Data Encryption Standard Complete The Above Chegg Com

Exam Questions For The Course Ttm Information Security May Part 1 Pdf Free Download
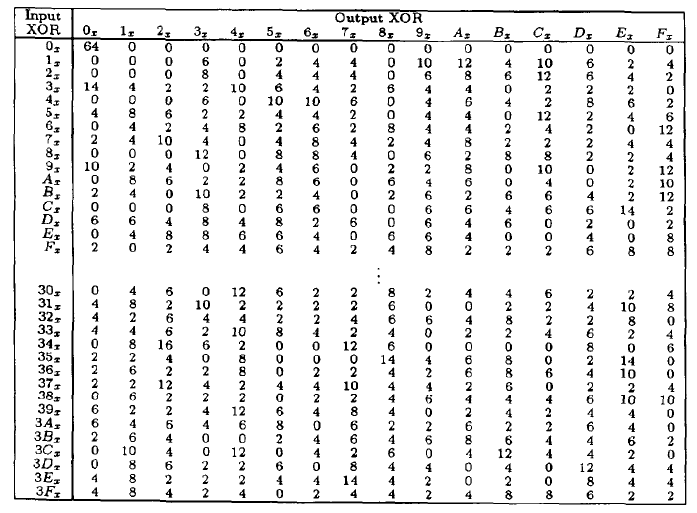
Differential Cryptanalysis On Data Encryption Standard Project 1 Security

Des Supplementary Material Wikipedia
Q Tbn And9gctyh9o 56tgq21pbmilijif Nvuag3kraor7vh6tcjrxyqyxz3q Usqp Cau
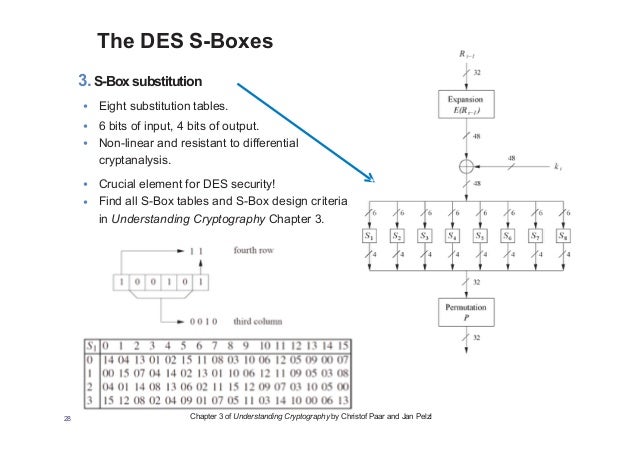
3 The Data Encryption Standard Des And Alternatives
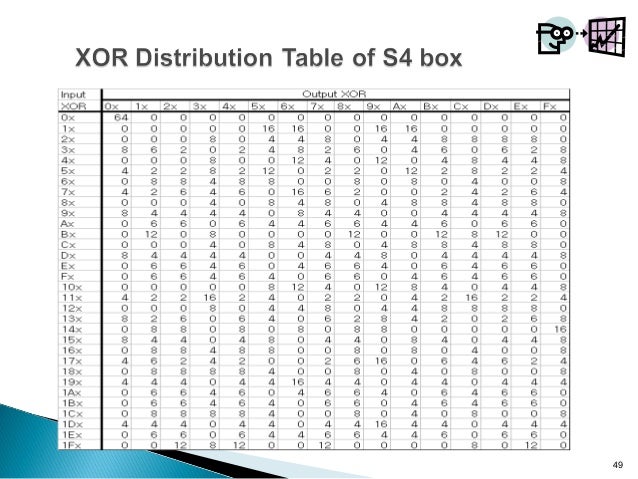
Des Block Cipher Hao Qi
Www Sans Org Reading Room Whitepapers Vpns S Box Modifications Effect Des Like Encryption Systems 768
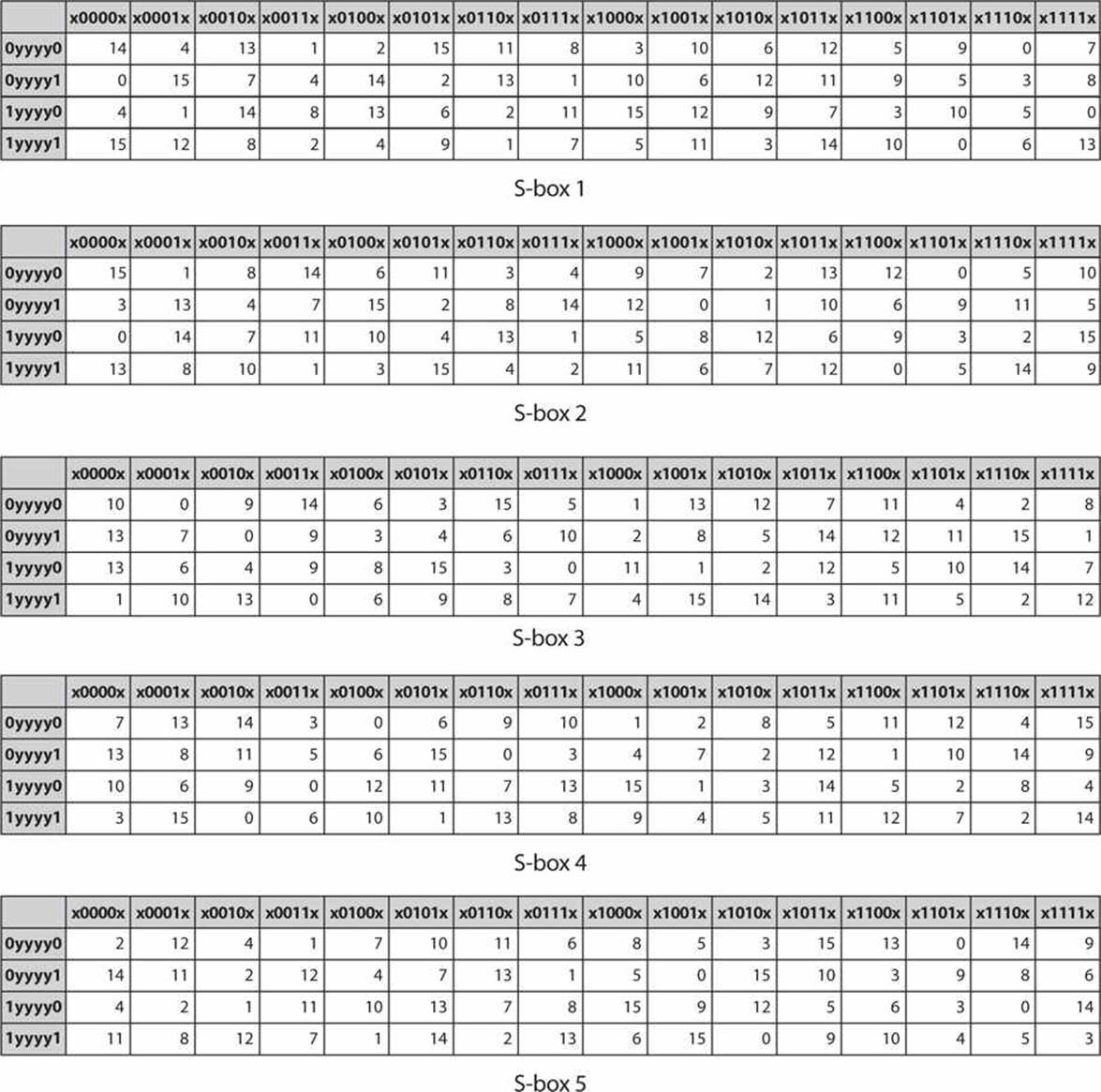
S Box Design Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16
Http Web Abo Fi Ipetre Crypto Lecture3 Pdf

Pdf What Do Des S Boxes Say To Each Other Semantic Scholar
Performance Factor Of Des S Boxes Bitslice Des S Boxes Vs Download Scientific Diagram
Ppt Ics 454 Principles Of Cryptography Powerpoint Presentation Free Download Id
Feistel Networks Symmetric Ciphers And Hashes Modern Cryptography Applied Mathematics For Encryption And Informanion Security 16
Solved Consider The Two S Boxes S1 And S2 Of Des Shown T Chegg Com
Http Www Cs Man Ac Uk Banach Comp Info Courseslides Wk2 1 Des Pdf

9 3 The Des S Boxes P Box And Initial Permutation Ip Computer Security And Cryptography Book
Http Www Cs Man Ac Uk Banach Comp Info Courseslides Wk2 1 Des Pdf

Des Algorithm S Box Learning Programmer Sought
Data Encryption Standard Wikipedia
Cryptography And Network Security Chapter 3 Ppt Download
1 How Many Bits Of Output Are Produced After Subs Chegg Com

Table 5 From Feistel Schemes And Bi Linear Cryptanalysis Semantic Scholar
6 1 2 Overview Des Is A Block Cipher As Shown In Figure Ppt Video Online Download

Scheme Presenting An Application Of S Boxes In The Des Algorithm On Download Scientific Diagram
Ppt Class Assignment Powerpoint Presentation Free Download Id

2 Datapath Of The Serialized Des Asic With Original S Boxes Download Scientific Diagram

File Des S Box Jpg Wikimedia Commons

Pdf What Do Des S Boxes Say To Each Other Semantic Scholar

Ch03 Testbank Crypto6e
Data Encryption Standard Des

Parametric Comparison Of Emds Algorithm With Some Symmetric Cryptosystems Sciencedirect

Des Encryption Youtube

Pdf Good S Boxes Are Easy To Find

Data Encryption Standard
A Extend The Input To 48 Bits Using Des Expansion Chegg Com
Differential Cryptanalysis On Data Encryption Standard Project 1 Security
Des Cipher
Referring To The Lecture Notes On Des There Are One Expansion Permutation Table1 Eight Substitution S Boxes And One Permutation P Box Table 2 Course Hero

Pdf What Do Des S Boxes Say To Each Other Semantic Scholar

Pdf What Do Des S Boxes Say To Each Other Semantic Scholar
Cryptography And Network Security Chapter 3 Ppt Download
S Box Design Springerlink

Step 3d S Box Substitution

What Is S Meant By S Box Row And Column In Des Cryptography Stack Exchange
Question Answer The Following Questions About S Boxes In Des A Show The Result Of Passing Through S Box 3 B Show The Result Of Passing Course Hero
Ppt Cryptography And Network Security Chapter 3 Powerpoint Presentation Id
Block Ciphers

Pdf What Do Des S Boxes Say To Each Other Semantic Scholar
Feistel Cipher Des Ppt Download

Ppt On Des Powerpoint Slides

How To Teach Des Using Python The Easy Way Part 2 Round Function F By Ajit Kumar Medium

Secret Key Crypotography
Q Tbn And9gcrkf7hktq2x0v Cofzbl Jg Hrfjci8qps8wyyhmjik1ssxscvm Usqp Cau
Cs480 Cryptography And Information Security Ppt Download
Data Encryption Standard Wikipedia
Section 3 2 The Data Encryption Standard Cryptography And Network Security 4th Edition

Pdf Extended Analysis Of Des S Boxes Semantic Scholar
Www Sans Org Reading Room Whitepapers Vpns S Box Modifications Effect Des Like Encryption Systems 768

Solved Question 8 5 Pts Consider The Two S Boxes S1 And 2 Chegg Com

Data Encryption Standard Des Ppt Download

Data Encryption Standard Des Set 1 Geeksforgeeks

9 3 The Des S Boxes P Box And Initial Permutation Ip Computer Security And Cryptography Book
S Box Design Springerlink

1 Compute The 4bit Output Using The Given S Boxes Chegg Com

Solved Exercises 11 Answer The Following Questions About Chegg Com

Pdf Extended Analysis Of Des S Boxes Semantic Scholar

Data Encryption Standard Des Ppt Video Online Download
Data Encryption Standard Wikipedia

How Can Des Have 6x4 S Boxes And Still Be Reversible Theoretical Computer Science Stack Exchange
Network Security Lec4
Ppt Network Security Powerpoint Presentation Free Download Id

6 Data Encryption Standard Des Pdf Free Download

Solved This Set Of Homework Is For The Contents Covered I Chegg Com




